What are slow HTTP Get&Post attacks?
Slow HTTP Get&Post attacks are a type of Application Layer Denial-of-Service (DoS) attack making Internet servers' resource unavailable by simply exhausting servers' TCP connections. For a HTTP server, the number of maximum concurrent TCP (and HTTP) connections is limited to a certain number, such as 5000 concurrent TCP connections for a Windows 2003 server. If a user makes a lot of concurrent TCP connections to exceed the maximum, the HTTP server will not response any more requests. Some tools were developed to launch Slow HTTP Get&Post attacks and the most famous ones are Slowloris HTTP Dos, OWASP HTTP Post tool and slowhttptest. These tools implement most common low-bandwidth Application Layer DoS attacks. The technical details are different, some create HTTP Get DoS attacks while others make HTTP Post DoS attacks.
Slow HTTP Get&Post attack can shut down on all Internet HTTP servers, including IIS servers, Apache servers and Nginx servers. Research data shows Internet servers increasingly suffer Slow HTTP Get&Post attack. Many facts contribute to it. One is the attacking pattern, which makes IDS systems harder to detect it. Slow HTTP Get&Post attack uses much less attacking resource and one regular computer can launch it. In addition, the attacking tools are easy-to-use for newbies.
The following picture shows OWASP HTTP Post Tool, which was created to test availability concerns from Layer7 DoS HTTP GET and HTTP POST DoS attacks.
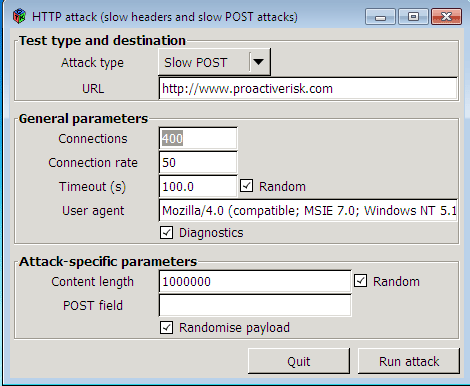
How to stop slow HTTP Get&Post attacks?
Anti DDoS Guardian stops Slow HTTP Get&Post attacks by limiting the TCP concurrent connection number for each client computer. If one client computer tries to access a Windows server with too many TCP connections, such as 30 concurrent connections, the client computer will be marked as suspicious and the IP address of that computer will be blocked for a certain period.
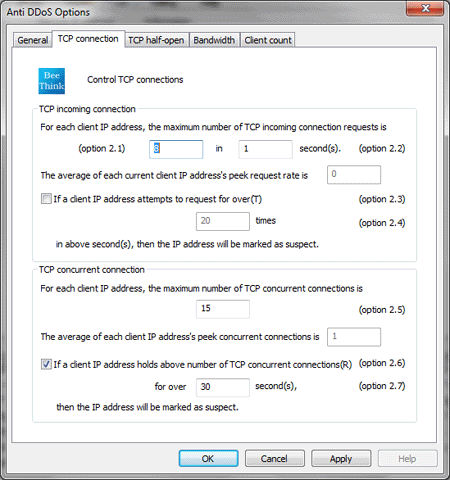
The option dialog of Anti DDoS Guardian is showed as above. Due to the options 2.5, 2.6, 2.7, an IP address will be blocked if it tries to make 15 concurrent TCP connections for over 30 seconds. In our tests, the Slow HTTP Get&Post attacks can be completely ceased.
Do you want to stop Slow HTTP Get&Post attacks right now?